
J. Cent. South Univ. (2018) 25: 2410-2422
DOI: https://doi.org/10.1007/s11771-018-3925-2
Smart control plane for information centric network-internet service provider networks
SEBAKOR Mahamah1, THEERA-UMPON Nipon1, 2, AUEPHANWIRIYAKUL Sansanee2, 3
1. Electrical Engineering Department, Faculty of Engineering, Chiang Mai University,Chiang Mai 50200, Thailand;
2. Biomedical Engineering Institute, Chiang Mai University, Chiang Mai 50200, Thailand;
3. Computer Engineering Department, Faculty of Engineering, Chiang Mai University,Chiang Mai 50200, Thailand
 Central South University Press and Springer-Verlag GmbH Germany, part of Springer Nature 2018
Central South University Press and Springer-Verlag GmbH Germany, part of Springer Nature 2018
Abstract:
The information centric network (ICN) has been widely discussed in current researches. The ICN interoperation with a traditional IP network and caching methods are one of the research topics of interest. For economic reasons, the capability of applying the ICN to internet service providers (ISPs) with various traditional IP protocols already implemented, especially IGP, MPLS, VRF, and TE, does not require any change on the IP network infrastructure. The biggest concern of ISPs is related to their customers’ contents delivery speed. In this paper, we consider ICN caching locations in ISP by using the concept of locator/ID separation protocol (LISP) for interoperation between a traditional IP address and name-based ICN. To be more specific, we propose a new procedure to determine caching locations in the ICN by using the cuckoo search algorithm (CSA) for finding the best caching locations of information chunks. Moreover, we create the smart control plane (SCP) scheme which is an intelligent controlling, managing, and mapping system. Its function is similar to the software defined network concept. We show how the proposed SCP system works in both synthetic small network and real-world big network. Finally, we show and evaluate the performance of our algorithm comparison with the simple search method using the shortest path first algorithm.
Key words:
Cite this article as:
SEBAKOR Mahamah, THEERA-UMPON Nipon, AUEPHANWIRIYAKUL Sansanee. Smart control plane for information centric network-internet service provider networks [J]. Journal of Central South University, 2018, 25(10): 2410–2422.
DOI:https://dx.doi.org/https://doi.org/10.1007/s11771-018-3925-21 Introduction
The current model of internet architecture is the host centric network (HCN) which is an end-to-end host communication that has certain limitations, such as publishing speed, volume bandwidth consumptions, over loading at responders, immobility addressing, latency, and so on. This has been even more serious in the internet of things (IoT) era in which more and more smart devices are capable of communicating to the internet [1, 2]. Recently, a better approach called the information centric network (ICN) has been widely discussed in several research papers and has proved to provide more benefits than the current IP network architecture. In essence, it consists of requester, publisher, naming, and caching. The ICN infrastructure is composed of numerous information chunks that are cached on the routers. As shown in Figure 1, chunks are stored and cached on router C.
The role of an ISP is to provide the best contents’ delivery speed to their customers. In order to implement the ICN, which possibly affects the ISP network equipment and configuration, ISPs do not require any dramatic changes in their IP network that have already deployed various traditional IP networks, such as interior gateway protocol (IGP), border gateway protocol (BGP), multiprotocol label switching (MPLS), and virtual routing and forwarding (VRF). ICN implementation on an ISP requires the IP-naming mapping as the main part of the interoperation between the ICN and the traditional IP network. In this paper, the concepts of locator/ID separation protocol (LISP) and software defined network (SDN) were used for both interoperation and caching location controlling.
The LISP is a protocol which creates two IP address: routing locators (RLOC) and endpoint identifiers (EID). Specifically, EIDs are end-host devices while RLOC is their location. A LISP mapping system is designed to perform a mapping and lookup between EID and RLOC.
In this work, we propose a method to find the best caching locations of information chunks by using the cuckoo search algorithm (CSA). We create the smart control plane (SCP) in order to get the best caching allocation. The SCP is rather similar to the SDN concept. Basically, the SDN consists of two parts: data plane and control plane. The data plane is used for data forwarding while the control plane acts as an intelligent controller. The difference between the proposed SCP and the SDN is that the SCP uses the CSA for finding the best caching allocation and IP-naming mapping while the current SDN has no such functionality.
This work is organized as follows. Section 2 describes related work that can be found in the literature. Section 3 explains the cuckoo search algorithm. The proposed approach and performance evaluation are presented in Sections 4 and 5, respectively. Finally, the conclusion and future work are described in Section 6.
2 Related works
In this section, we briefly discuss some related work of ICN approaches, CSA, SDN, and LISP concept. Moreover, we also describe related developments in the area of the IP and ICN interoperation.
Many recent papers have proposed alternate methods, studied, and surveyed existing researches on the ICNs [3, 4]. The main aim of those surveys was to briefly describe the functions of ICN architectures, i.e., data oriented network architecture (DONA), publish-subscribe internet technology (PURSUIT), scalable and adaptive internet solutions (SAIL), content mediator architecture for content-aware networks (COMET), CONVERGENCE, and MobilityFirst. These methods can be divided into two naming types. The first is human-readable, such as the content centric networking (CCN) and named data networking (NDN) [5], which is similar to the traditional web URL. The second naming type is based on self- certifying which is not human-readable, such as DONA architecture [6]. Many named information retrieval methods for ICNs were also proposed, e.g., name-based resolution, name-based routing, multicast, etc.
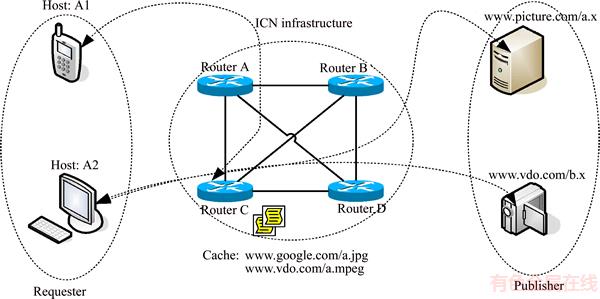
Figure 1 ICN architecture
Efforts on new routing for the ICN architecture appear in many research papers, for example, the name-based resolution method that replaces the name-based ICN with legacy IP routing. It can be used by the LISP concept [7, 8]. Other new approaches used the network layer locator, MsgID, MPLS and SDN for forwarding the ICN packets [9–14]. In Ref. [15], the requested ICN packets were forwarded through the service layer and replied through network layer. In Ref. [16], the controllers that controlled ICN packets were used. The approach in this mentioned paper was rather similar to a cloud controller used in our approach presented here. However, there are some different points, such as a set of root controllers and a set of area controllers. Some methods for finding the optimized caching locations utilized multicast, nearest user requested, and load distribution [17–19]. Most of the papers only proposed an algorithm for the best nearest destination of caching server and timer count of caching method. The importance of network information, such as best path reachability and caching location finding algorithm, was not considered.
3 Cuckoo search algorithm
The cuckoo search algorithm (CSA) is a metaheuristic optimization algorithm developed by YANG et al [20]. The concept of CSA is based on the behavior of a cuckoo bird. A cuckoo bird lays its eggs into the nest of other birds. If other birds found that the eggs are not their own, they will destroy those eggs or abandon their nest and build a new one elsewhere. The CSA consists of eggs and nests, with the fixed number of nests. It is based on two main ideas. First, each cuckoo bird lays its egg in a nest randomly. Second, the best nest with the best egg will be assigned as the next generation. The CSA algorithm can be described by the following pseudocode [20]:
Objective function f(x), x=[x1, …, xn]T
Generate an initial population of host nests;
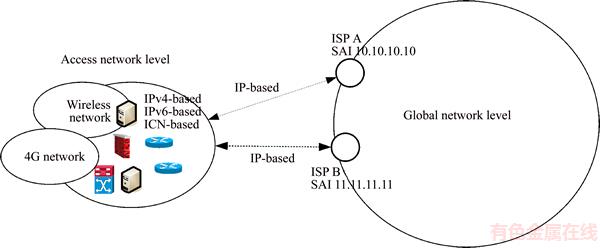
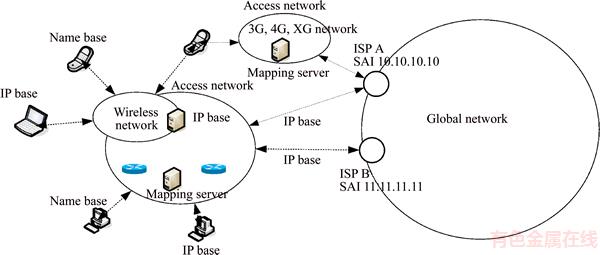
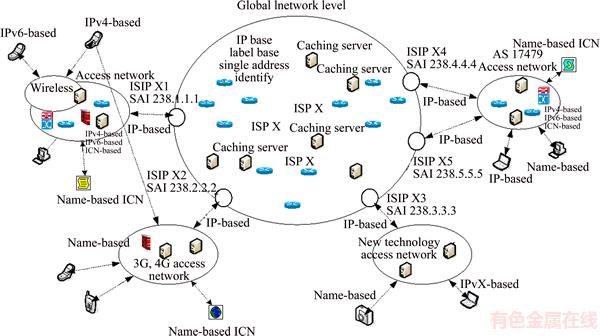
While (t Choose randomly a nest among n (says, j); if (Fi>Fj) Replace j by the new solution; end if A fraction (pa) of worse nests are abandoned and new ones/solutions are built/generated; Keep best solutions (or nests with quality solutions); Rank the solutions and find the current best; end while Postprocess results and visualization; Hence, the two primary operators of CSA include the local and global explorative random walks [21]. The local random walk relates to abandoning worse nests behavior, i.e., where where α is a scaling factor, L(b) is Lévy distribution with parameter β. In the library provided by the inventors of CSA, the term L(β) is computed as follows [22]: where s, u and v are drawn from normal distribution, i.e., s~N(0, 4 Proposed method The main objective of caching allocation is to enable the publishing to be faster and reduce publisher overloading. Many researchers have proposed methods that support caching schemes in the ICN architecture. In our approach, we use the CSA for finding the optimal router locations which is faster than other algorithms and can distribute router’s caching overloading. Meanwhile, the smart control plane (SCP) requires the information of network topology, link connection, link capacity, and load of router. The SCP is responsible for the control plane while network devices are for the data forwarding plane. The proposed SCP consists of two main methods, i.e., IP-ICN interoperation and caching allocation. We describe both of them as follows. 4.1 IP-ICN interoperation method In the ICN, information (I) consists of the number of chunks in which each chunk has the unique name (nij). For example, I1={n11, n12, …,n1j} so that Figure 2 Address encapsulation In the ISP domain, we divide the ISP network into two domains, i.e., transit network domain and end domain. The transit network domain is only for forwarding and caching the information chunks in which its router, called the content store (CS), is capable of caching. It uses IGP routing for connection reachability of AI. The end domain can be an end-host requester, end-host publisher device, or end service objects. It can be in the form of either IP-based or name-based. Let the requester be Rn while publisher is Pn as shown in Figure 3. From the example, the desired information is composed of a number of chunks represented by I1={n11, n12, n13, n14}. It originates from P1 which is located outside the ISP domain. The ISP is composed of a number of routers, all of them supporting ICN caching. Let A be the set of AI of routers, hence an∈A. Each an will learn the IGP routing and create a connection reachability. From the figure, publisher P1 sends register messages to the SCP, and the SCP inserts P1→a6 and P1→a7 into its mapping table. Let us consider the case that the requester R1 is interested in I1. Firstly, it sends the register message about its location to the SCP. After that, the SCP inserts R1→a1 into its mapping table. Secondly, R1 asks the SCP about AI of I1. The SCP replies to R1 that I1 is at a6 or a7. After that, R1 encapsulates the packet into a1. Then a1 consults the routing table and then forwards that packet to a6 or a7. When the packet arrives at a6 or a7, the destination router knows that this is the destination address of this packet, and thus, it asks the SCP about the name-based address. Then the decapsulation occurs and a message is sent to P1. This is similar to the LISP concept. While publishing the information, publisher P1 distributes the chunks into the network. Some chunks are cached on some routers. From the figure, chunk n11 and n12 are cached on a3 and a5, respectively. Those routers send the chunk caching location messages to the SCP. If R2 is interested in I1, the same process as earlier described takes place. Messages are sent to the SCP asking about I1. The SCP knows that I1 is composed of {n11, n12, n13, n14} and it knows that n11 and n12 are located on a3 and a5, respectively. The SCP then replies the message that n11 and n12 are located on a3 and a5, respectively, while other chunks are located at the source of publisher P1. Figure 3 Example of ICN-ISP network For our IP-ICN interoperation design, we divide the current internet network into three levels: global network level, access network level, and access object level. 1) The global network level is composed of a number of ISPs. At this level, each ISP uses IP-based connectivity. However, intradomain connection in each ISP still uses IGP. The ISPs peering also uses the BGP for route exchanging. We propose the single address identification (SAI) on each ISP and use our approaches for creating the best path reachability. In each ISP, we group all routers in this domain into a single address and identify this address as the SAI. Then the cloud controller advertises the SAI to the global network. 2) The access network level is the enterprise or local network, e.g., LAN network, 3G network, 4G network, and other technologies. The access network and the global network attach to SAIs. The IP prefixes or alternate addresses are registered in the cloud controller which maps each IP prefix in the access network level to SAI. Each IP prefix is unique and authorized by the internet assigned number authority (IANA) similar to the existing internet architecture. For example, IP prefix which are 202.28.0.0/24, 202.29.0.0/24 in the access network level, are mapped to the same SAI like 10.0.0.1. Figure 4 shows an access network level that supports IP-based network addressing which are IPv4-based, IPv6-based and name-based. It demonstrates three network types, i.e., LAN, wireless, and 4G network. Besides, firewall, servers, routers, and switches are also attached. 3) The access object level incorporates various addressing schemes with the current internet network. An access object is the end address of devices or services. The object address must be unique and it is sometimes in name-based ICN format which consists of information chunk and caching objects. Moreover, besides ICN, other new technologies are also supported by our approaches. Figure 5 shows that IPv4 devices, IPv6 devices, name-based ICN, and other new applications addressings are registered to the local mapping server. Figure 4 Example of access network level in proposed IP-ICN interoperation Figure 5 Example of access object level in proposed IP-ICN interoperation When all 3 components are combined together, an example of the overall proposed IP-ICN interoperation is as shown in Figure 6. 4.2 Caching allocation In caching allocation, we use the CSA where each chunk represents a cuckoo egg and each router represents a nest. Hence, our caching allocation scheme consists of five steps: Chunk selection; LinkAct matrix initialization; Chunk laying on the routers or nests; Nest destroying and rebuilding; Next generation moving. Chunk selection is the method of creating the chunk counter table (CCT) and selecting the best chunk that will be cached based on its popularity and frequency of request rate. The frequency of request rate (Hitrate) of chunk n can be calculated by where Rn is the number of users who are interested in chunk n. After that we randomly initialize a matrix called LinkAct(0) where each of its element where k is the total number of links and l is the number of random formats generated. The value of l is to be set by the users. Chunk laying is the process of randomly placing those chunks on each router by using the CSA. After that, the metric for the ith router based on the shortest path first (SPF) algorithm is calculated by where SPFMetrici is the sum of metrics that we try to lay a chunk on nodes or routers with the assigned AI (ai). Moreover, the fair-share rate of the ith router (Fi) is used to distribute and find the best loading of the routers. It can be calculated by where NodeCapi and NodeActi are the router caching capacity and actual caching load of router i, respectively. Figure 6 Example of proposed IP-ICN interoperation Three parameters are extracted for the ith router as follows: The fitness function of the ith nest (router) is calculated by Figure 7 Small network model considered in this work Table 1 SPF metric for each address identification Table 2 X element for each router where m is the number of nests (routers in this research) and i is the router’s number from the beginning position to the last position (m). n is the number of parameters, equal to 3 here. The optimal solution of caching locations is obtained from the minimum fitness function based on the current LinkAct matrix using the CSA. It is clearly seen that the CSA considers the criteria of the shortest path (parameter xi1), the frequency of request rate (parameter xi2), and the fair-share rate (parameter xi3), as shown in Eq. (6) to Eq. (12), to find the optimal caching location for each information chunk. For the global explorative random walk, only the best format (row of LinkAct matrix) corresponding to the minimum fitness function is kept for the next generation. The remaining l-1 formats will be destroyed and then rebuilt based on Levy flight. Consider In the experiments, the CSA parameters were set according to the default values in the library provided by the CSA inventors as follows: s=1.0, β=1.5, ss=1.0, sv=1.0, and and G is the standard Gamma function [22]. The next step is the local random walk which is performed according to Eq. (1), i.e., We, once again, adopt the default parameters as follows: s=1.0, pa=0.25, a is a random number drawn from a uniform distribution, i.e., α~U [0, 1], and e is a random number drawn from a uniform distribution, i.e., e~U [0, 1]. The new 5 Results and discussion In this section, we investigate the performance of the proposed algorithm by means of simulation. The experiments are performed on a small network and a real-world big network. The comparison with the simple searching (SS) method, which uses standard SPF algorithm, is also performed. As for the simulation environment, we use GNS3 version 0.8.4 and the Cisco IOS software version 15.2(4) S5 running on a Windows 10 Education with 4.00 GB RAM, Intel(R) core(TM) 2 CPU 2x3.00 GHz, 64-bit operation system, x64-based processor. The caching allocation methods are implemented using Matlab 8.3.0.532 running on a Windows 8.1 Pro, Intel(R) core (TM) 2 duo CPU 2x2.40GHz. 5.1 Results on small network In this simulation, the setup is as follows. There are 8 routers and 3 chunks, i.e., n1, n2, and n3. The users who are interested in n1 and n2 chunks are attached to r2 and r8 while n3 is attached to r3, r2, and r7. Link capacity of each router is 10 Mbps. Router’s caching loading capacity is 100 units and chunk size is 1 unit. At the beginning, we first select the popular chunks then create the matrix of the frequency of request rate (Hitrate). In the first generation, we randomly initialize the LinkAct matrix whose rows represent the formats. The initial LinkAct contains 25 formats (l=25), each one in the range of 0 to 10 Mbps. As shown in Figure 8, the fitness values of each generation of n1 (Figure 8(a)), n2 (Figure 8(b)), and n3 (Figure 8(c)) chunks gradually decreases until a stopping criterion is reached. We compare the proposed algorithm with the simple search (SS) method. The best locations obtained from our method compared to the SS method are shown in Table 3. The results show that our method yields the best locations of n1, n2, and n3 at the routers r1, r2, and r3, respectively. On the other hand, the SS method yields the result that n1 is located in any router within the set {r1, r2, r3, r5, r7, r8}. Likewise, n2 and n3 are located in any router within the sets {r1, r2, r3, r5, r7, r8} and {r2, r3, r7}, respectively. The results show that the proposed method yields more favorable outcomes, i.e., only one caching location for each information chunk. In contrast, the SS method yields many possible locations for each information chunk because these routers have the same nearest distance to the clients. 5.2 Results on real-world big network In this simulation, we use a network model of Inter University Network (UniNet) as shown in Figure 9. UniNet is a Thai ISP for education and research network. It consists of 120 routers covering the entire Thailand. In this research, we only focus on 52 routers that are located in the northern and northeastern regions of Thailand. We then assume that there are 3 information: I1={n11, n12, n13}, I2={n21, n22, n23}, and I3={n31, n32, n33,n34}. The users who are interested in chunks nij are shown in Table 4. We intentionally assume that there are 2 users who are interested in n13 which are attached to r13. As before, link capacity of each router is 10 Mbps. Router’s caching loading capacity is 100 units and chunk size is 1 unit. The process of creating the Hitrate matrix is the same as in the previous experiment. Once again, the initial LinkAct matrix contains 25 formats, each one in the range of 0-10 Mbps. Figure 8 Fitness plots of chunks n1 (a), n2 (b), and n3 (c) from proposed method on small network shown in Figure 7 Table 3 Comparison between proposed method and simple searching method on small network shown in Figure 7 Figure 9 UniNet backbone in northern and northeastern regions of Thailand Table 4 Chunks and their corresponding interested users As shown in Figure 10, the fitness values of each generation of n11 (Figure 10(a)), n12(Figure 10(b)), n13(Figure 10(c)), n21 (Figure 10(d)), n22 (Figure 10(e)), n23 (Figure 10(f)), n31(Figure 10(g)), n32 (Figure 10(h)), n33 (Figure 10(i)), and n34 (Figure 10(j)) chunks gradually decreases until the routers are not changed. Once again, we compare our algorithm with the SS method. The best locations obtained from our method compared to SS method are shown in Table 5. The results of our method show that the best locations of n11, n12, n13, n21, n22, n23, n31, n32, n33, and n34 are at the routers r35, r23, r13, r14, r42, r36, r46, r24, r16 and r23, respectively. However, the simple SS method shows that n11 is located in any router within the set {r35, r36, r37, r38, r41, r42, r43, r44, r48}. Likewise, n12, n13, n21, n22, n23, n31, n32, n33, and n34 are located in any routers within the sets {r17, r20, r23}, {r13, r17, r20, r23}, {r14, r15, r16, r17}, {r35, r42},{r36, r37}, {r46, r47, r48, r49, r50, r51}, {r23, r24, r25, r31, r32}, {r14, r16, r18, r27, r28} and {r23, r24}, respectively. Figure 10 Fitness plots of chunks nij from proposed method on real-world big network shown in Figure 9 Table 5 Comparison between proposed method and simple search method on real-world big network shown in Figure 9 From the results, it can be clearly seen that the SS method yields so many possible caching locations for each chunk. This is because these locations (routers) have the same nearest distance to the destinations. From the derived set of routers, we will have to select a proper one for each chunk which is a tedious task to come up with the best combination. The results show that using the nearest distance only is not adequate to determine the proper caching locations. Meanwhile, the proposed method which takes into account not only the shortest path (parameter xi1), but also the frequency of request rate (Hitrate) (parameter xi2), and the fair-share rate (parameter xi3), yields one caching location for each information chunk. This is a very favorable output from the contents publishing speed and routers’ caching load balancing. 6 Conclusions We propose a new smart control plane (SCP) scheme which takes care of controlling, managing, and mapping of the information centric network (ICN) data chunks. The proposed SCP exploits the cuckoo search algorithm to determine the best caching locations of information chunks. As a result, the proposed method can allocate chunks on the best routers which eventually increase contents’ publishing speed and distribute routers’ caching overloading. The proposed SCP scheme, consisting of the IP-ICN interoperation and caching allocation methods, is then an alternative of applying the information centric approach on top of the current IP-based technology without changing the current network physical structures. The main functions of the proposed SCP can be considered in two aspects: 1) For intradomain communication, the SCP performs the CSA to allocate the best caching locations of chunks. It creates the ISP’s SAI and automatically generates the configuration for all routers in the entire ISP in seamless network fashion. The SCP also has the duty to maintain the mapping between the name- based ICN and AIs inside the ISP or access network community. 2) For interdomain communication, the proposed SCP establishes and exchanges the mapping databases among domains, for example, ISPs-to-ISPs or access networks-to- ISPs. It also initiates and manages mapping of the name-based ICN with SAIs to communicate among ISPs and/or access networks. Like in the domain name servers (DNSs) in the current technology, a system for the smart control plane (SCP) is responsible to vast calculation and data storage. Therefore, the high performance server is required. We are currently investigating the possibility of applying the distributed approach to share the computation load and data storage, and ultimately, to reduce the number of requests to one particular SCP server which is the case of the lone SCP server scenario. In practice, although the network topology is changed after the initial setup, the routers in the network will send information about new routers’ links to the SCP. The SCP then rebuilds the new topology accordingly. This could happen from time to time (e.g., every hour or every week) depending on the network administrators’ consideration. Not only for the network topology, the SCP timely recalculates the optimal buffer positions using the cuckoo search algorithm. The SCP determines the new optimal places and moves the corresponding chunks there. Acknowledgments The authors would like to thank Inter University Network (UniNet) Thailand for the data applied in this research. We also thank Kittichai Wantanajittikul and Luis Frazao for their suggestions. The authors would like to thank the anonymous reviewers very much for their valuable comments leading to a huge improvement of this work. References [1] ABU-ELKHEIR M, HAYAJNEH M, ALI N A. Data management for the internet of things: Design primitives and solution [J]. Sensors, 2013, 13: 15582–15612. [2] KIBRIA M G, FATTAH S M M, JEONG K, CHONG I, JEONG Y K. A User-centric knowledge creation model in a web of object-enabled internet of things environment [J]. Sensors, 2015, 15:24054–24086. [3] XYLOMENOS G, VERVERIDIS C N, SIRIS V A, FOTIOU N, TSILOPOULOS C, VASILAKOS X, KATSAROS K V, POLYZOS G C. A survey of information-centric networking research [J]. IEEE Communications Surveys & Tutorials, 2014, 16(2): 1024–1049. [4] BARI M F, CHOWDHURY S R, AHMED R, BOUTABA R, MATHIEU B. A survey of naming and routing in information-centric networks [J]. IEEE Communications Magazine, 2012, 50: 44–53. [5] JACOBSON V, SMETTERS D K, THOMTON J D, PLASS M F, BRIGGS N H, BRAYNARD R L. Networking named content [C]// International Conference on Emerging Networking Experiments and Technologies. Rome: IEEE, 2009: 1–12. [6] KOPONEN T, CHAWLA M, CHUN B G, ERMOLINSKIY A, KIM K H, SHENKER S, STOICA I. A data-oriented (and beyond) network architecture [C]// Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications. Kyoto: ACM, 2007: 181–192. [7] YUAN S, LIN T, ZHANG G, LI Y, TANG H, CI S. A future anycast routing scheme for information-centric network [C]// Asia-Pacific Conference on Communications. Jeju island: IEEE, 2012: 173–178. [8] AIASH M, MAPP G, KALLASH M M. Supporting communication in information centric networks using the location/ID split protocol and time released caching [C]// International Conference on Cloud Computing. Riyadh: IEEE, 2015: 1–6. [9] ZHU Y, NAKAO A. A deployable and scalable information- centric network architecture [C]// IEEE International Conference on Communications. Budapest: IEEE, 2013: 3753–3758. [10] VAHLENKAMP M, SCHNEIDER F, KUTSCHER D, SEEDORF J. Enabling ICN in IP networks using SDN [C]// IEEE International Conference on Network Protocols. Gottingen: IEEE, 2013: 1–2. [11] WANG J, GAO W, LIANG Y, QIN R, WANG J, LIU S. SD-ICN: An interoperable deployment framework for software-defined information-centric networks [C]// IEEE Conference on Computer Communications Workshops. Toronto: IEEE, 2014: 149–150. [12] REN J, LU K, WANG S, WANG X, XU S, LI L, LIU S. VICN: Versatile deployment framework for information- centric networks [J]. IEEE Network, 2014, 28: 26–34. [13] SAROLAHTI P, OTT J, KANGASHARJU J. Locations vs. identities in internet content: Applying information-centric principles in today’s networks [J]. IEEE Communications Magazine, 2012, 50:54–59. [14] SHAILENDRA S, PANIGRAHI B, RATH H K, SIMBA A. A novel overlay architecture for information centric networking [C]// National Conference on Communications. Mumbai: IEEE, 2015: 1–6. [15] WU Q, LI Z, ZHOU J, JIANG H, HU Z, LIU Y, XIE G. SOFIA: Toward service-oriented information centric networking [J]. IEEE Network, 2014, 28:12–18. [16] GAO S, ZENG Y, LUO H, ZHANG H. Scalable area-based hierarchical control plane for software defined information centric networking [C]// International Conference on Computer Communication and Networks. Shanghai: IEEE, 2014: 1–7. [17] SADJADPOUR H R. A new design for Information Centric Networks [C]// Annual Conference on Information Sciences and Systems. Princeton: IEEE, 2014: 1–6. [18] LIM S H, KO Y B, JUNG G H, KIM J, JANG M W. Inter-chunk popularity-based edge-first caching in content- centric networking [J]. IEEE Communications Letters, 2014, 18:1331–1334. [19] YUAN S, TANG D, LIU Y, BAI S, LIN T, CI S. Context- aware distributed service provisioning based on anycast for information-centric network [C]// International Conference on Computer Communication and Networks. Shanghai: IEEE, 2014: 1–7. [20] YANG X S, DEB S. Cuckoo search via Lévy flights [C]// World Congress on Nature Biologically Inspired Computing. Coimbatore: IEEE, 2009: 210–214. [21] YANG X S, Nature-inspired optimization algorithms [M]. Amsterdam: Elsevier, 2014. [22] YANG X S, DEB S. Multiobjective cuckoo search for design optimization [J]. Computer & Operations Research, 2013, 40: 1616–1624. (Edited by HE Yun-bin) 中文导读 信息中心网络-互联网服务提供商网络的智能控制平面 摘要:信息中心网络(ICN)在当前的研究中得到广泛的讨论。而ICN与传统IP网络的互操作和缓存方法是当前研究热点。出于经济原因,将ICN应用于互联网服务提供商(ISP)不需要对IP网络基础设施进行任何更改,这些服务提供商具有各种已经实现的传统IP协议,特别是IGP、MPLS、VRF和TE。互联网服务提供商最关心的是客户的内容交付速度。本研究使用定位器/ID分离协议(LISP)的概念在传统IP地址和基于名称的ICN之间进行互操作,从而考虑了ISP中的ICN缓存位置。更具体地说,提出了一种新的程序,通过使用布谷鸟搜索算法(CSA)来确定ICN中的缓存位置,以找到信息块的最佳缓存位置。此外,还创建了智能控制平面(SCP)方案,这是一个智能控制、管理和映射系统。其功能类似于软件定义的网络概念。展示了所提议的SCP系统如何在合成小网络和现实世界大网络中工作。最后,展示并评估了本文算法与使用最短路径优先算法的简单搜索方法的性能比较。 关键词:信息中心网络(ICN);智能控制平面;缓存分配;IP-ICN互操作;布谷鸟搜索算法 Received date: 2017-09-02; Accepted date: 2018-01-23 Corresponding author: THEERA-UMPON Nipon, PhD; Tel: +66–5394–4140; E-mail: nipon@ieee.org; ORCID: 0000-0002-2951-9610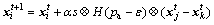 (1)
(1) is the ith solution at time t,
is the ith solution at time t, 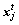 and
and 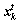 are two different randomly selected solutions, α is a scaling factor, s is the step size, H(u) is a Heaviside function, pa is the preset probability of worse nests to be abandoned, e is a random number drawn from a uniform distribution, and
are two different randomly selected solutions, α is a scaling factor, s is the step size, H(u) is a Heaviside function, pa is the preset probability of worse nests to be abandoned, e is a random number drawn from a uniform distribution, and  denotes the entry- wise product of two vectors. Meanwhile, the CSA explores the search space using Lévy flights to decide whether to lay an egg or get a cuckoo. This operation is referred as the global explorative random walk, i.e.,
denotes the entry- wise product of two vectors. Meanwhile, the CSA explores the search space using Lévy flights to decide whether to lay an egg or get a cuckoo. This operation is referred as the global explorative random walk, i.e.,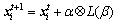 (2)
(2)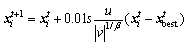 (3)
(3)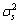 ), u~N(0,
), u~N(0,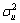 ), and v~N(0,
), and v~N(0,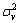 ), respectively,
), respectively, 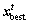 is the best solution at time t.
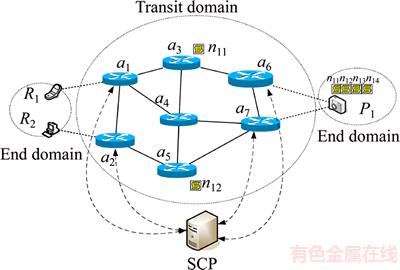
is the best solution at time t. nij∈I. In the LISP architecture, the EID address is encapsulated in an RLOC address. RLOC is used for routing and forwarding. As a result, only RLOC addresses are advertised to the network. In the case of name-based identification, the SCP uses the LISP concept in that the name-based ICN of chunks will be encapsulated with IP address identification (AI). This is the key of our research. The AI learns about routing and forwarding the packet to a traditional IP network. Once it traverses to the edge router, the packets are decapsulated and forwarded to the end requester. For mapping system, the name-based ICN will be mapped into AI. Each pair of source and publisher is registered to the SCP mapping table while the ICN packet will be encapsulated in the format shown in Figure 2.
nij∈I. In the LISP architecture, the EID address is encapsulated in an RLOC address. RLOC is used for routing and forwarding. As a result, only RLOC addresses are advertised to the network. In the case of name-based identification, the SCP uses the LISP concept in that the name-based ICN of chunks will be encapsulated with IP address identification (AI). This is the key of our research. The AI learns about routing and forwarding the packet to a traditional IP network. Once it traverses to the edge router, the packets are decapsulated and forwarded to the end requester. For mapping system, the name-based ICN will be mapped into AI. Each pair of source and publisher is registered to the SCP mapping table while the ICN packet will be encapsulated in the format shown in Figure 2.
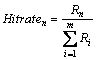 (4)
(4)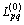 is the initial bandwidth of each link (pq), i.e.,
is the initial bandwidth of each link (pq), i.e.,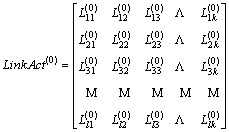 (5)
(5)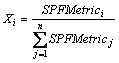 (6)
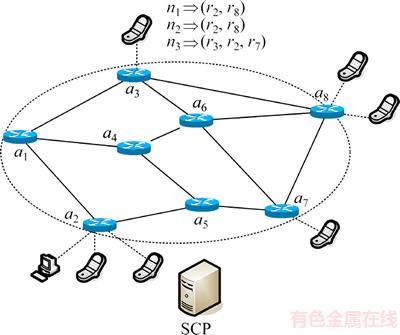
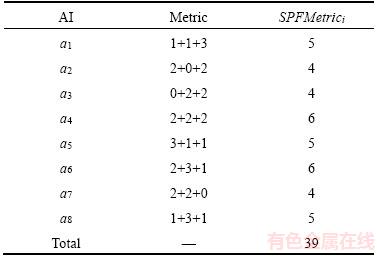
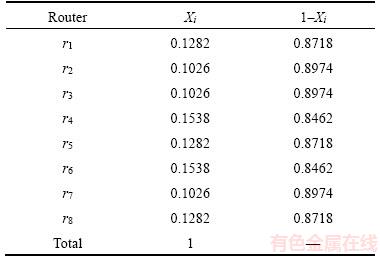
(6)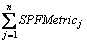 is the total of possible metrics that the chunk is laid on all routers. We use a network model shown in Figure 7 as an example for easier understanding of how the proposed method works. If the cost of each link is 1 and the requester who is interested in the chunk n3 are r3, r2, and r7, then the results of SPFMetrici are shown in Table 1, while the corresponding X and 1-X are shown in Table 2. It is worthwhile noting that the summation of all X is equal to 1 as shown by
is the total of possible metrics that the chunk is laid on all routers. We use a network model shown in Figure 7 as an example for easier understanding of how the proposed method works. If the cost of each link is 1 and the requester who is interested in the chunk n3 are r3, r2, and r7, then the results of SPFMetrici are shown in Table 1, while the corresponding X and 1-X are shown in Table 2. It is worthwhile noting that the summation of all X is equal to 1 as shown by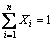 (7)
(7)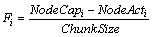 (8)
(8)
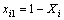 (9)
(9)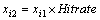 (10)
(10)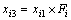 (11)
(11)
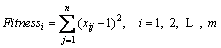 (12)
(12)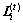 which denotes the ith row of LinkAct matrix, the cuckoo search with Lévy flight is performed as shown in Eq. (3) to find the new link rate
which denotes the ith row of LinkAct matrix, the cuckoo search with Lévy flight is performed as shown in Eq. (3) to find the new link rate 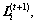 i.e.,
i.e.,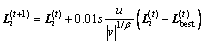 (13)
(13)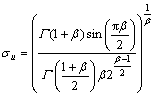 (14)
(14)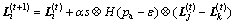 (15)
(15) are used to create the new LinkAct(t+1) matrix for the next generation. The search is kept going until the selected nests (routers) are not altered in two consecutive generations. It is worthwhile noting that the parameter l which is the number of random formats generated in each generation should be selected carefully. Too large value of l will yield very long time to converge. On the other hand, too small value of l will limit the search space. In our experiments, we initially selected l=25 which is the default value recommended in the CSA library written by the inventors of CSA [20–22]. We found that this value works well, yielding correct solution with fast convergence. We tried to apply larger values of l, but the algorithm yielded the same solution with much longer time to converge. Hence, we finally choose l=25 in our experiments.
are used to create the new LinkAct(t+1) matrix for the next generation. The search is kept going until the selected nests (routers) are not altered in two consecutive generations. It is worthwhile noting that the parameter l which is the number of random formats generated in each generation should be selected carefully. Too large value of l will yield very long time to converge. On the other hand, too small value of l will limit the search space. In our experiments, we initially selected l=25 which is the default value recommended in the CSA library written by the inventors of CSA [20–22]. We found that this value works well, yielding correct solution with fast convergence. We tried to apply larger values of l, but the algorithm yielded the same solution with much longer time to converge. Hence, we finally choose l=25 in our experiments.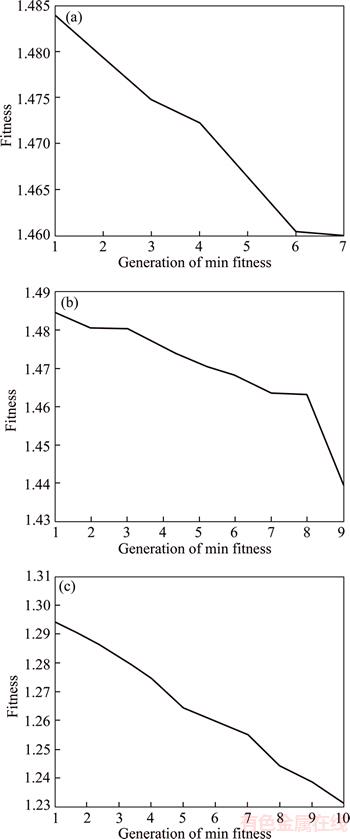
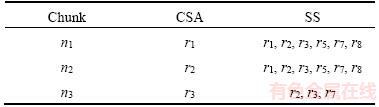
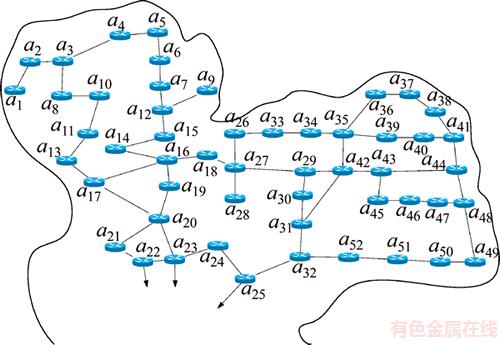
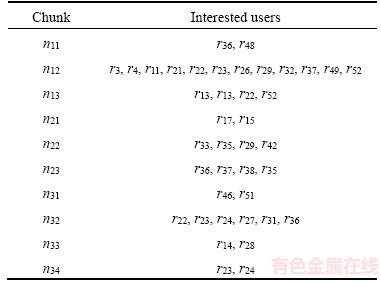
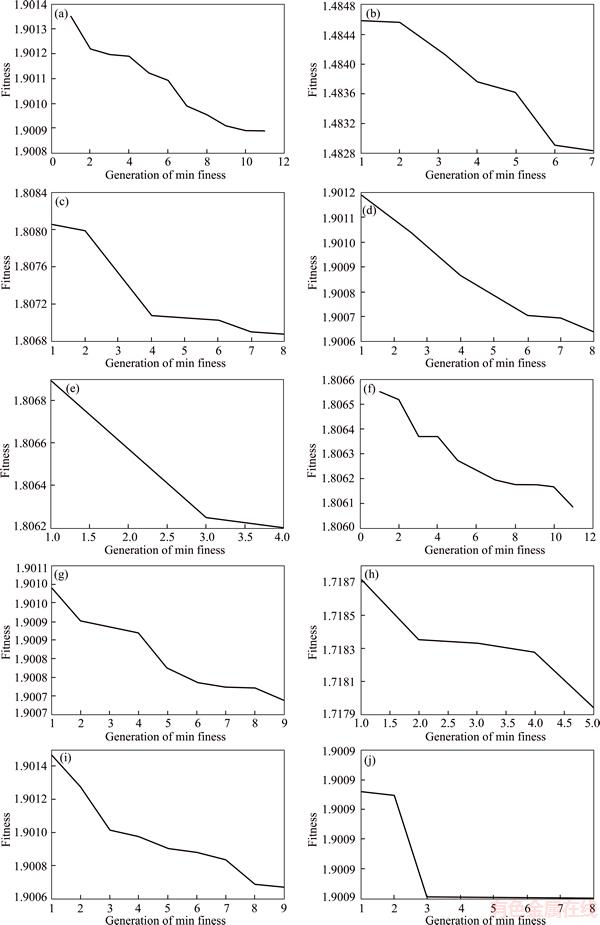

Abstract: The information centric network (ICN) has been widely discussed in current researches. The ICN interoperation with a traditional IP network and caching methods are one of the research topics of interest. For economic reasons, the capability of applying the ICN to internet service providers (ISPs) with various traditional IP protocols already implemented, especially IGP, MPLS, VRF, and TE, does not require any change on the IP network infrastructure. The biggest concern of ISPs is related to their customers’ contents delivery speed. In this paper, we consider ICN caching locations in ISP by using the concept of locator/ID separation protocol (LISP) for interoperation between a traditional IP address and name-based ICN. To be more specific, we propose a new procedure to determine caching locations in the ICN by using the cuckoo search algorithm (CSA) for finding the best caching locations of information chunks. Moreover, we create the smart control plane (SCP) scheme which is an intelligent controlling, managing, and mapping system. Its function is similar to the software defined network concept. We show how the proposed SCP system works in both synthetic small network and real-world big network. Finally, we show and evaluate the performance of our algorithm comparison with the simple search method using the shortest path first algorithm.


